55+ pages brute force attack detection using wireshark 3mb. This can be performed using certain tools such as Brutus THC Hydra Medusa Burp Suite intruder and many other tools available online. Flooding attack detection using anomaly techniques with wireshark. Brute force attacks are used for detecting login credentials using random combinations of username and passwords. Read also attack and understand more manual guide in brute force attack detection using wireshark Brute Force attack detection using wireshark.
Defining Brute Force A brute force attack is a trial and error method used to discover a password by systematically trying every possible combination of letters numbers and symbols until the correct combination is found. Brute-force attacks usually will not produce non-standard loads on the network and the way they are discovered is usually by IDS systems or when there is a suspicion that someone is trying to hack into the network.

The Reaver Tool Running A Brute Force Attack Against The Wps Passcode Download Scientific Diagram
| Title: The Reaver Tool Running A Brute Force Attack Against The Wps Passcode Download Scientific Diagram |
| Format: eBook |
| Number of Pages: 217 pages Brute Force Attack Detection Using Wireshark |
| Publication Date: August 2020 |
| File Size: 3.4mb |
| Read The Reaver Tool Running A Brute Force Attack Against The Wps Passcode Download Scientific Diagram |
 |
This can be performed using certain tools such as Brutus THC Hydra Medusa Burp Suite intruder and many other tools available online.

Brute force attack using LDAP simple bind. The 7 layers of OSI model helps you know exactly. Network intrusion detection using pattern matching. In a brute-force attack the attacker attempts to authenticate with many different passwords for different accounts until a correct password is found for at least one account. Brute-force attacks are a prevalent phenomenon that is getting harder to successfully detect on a network level due to increasing volume and encryption of netwo Brute Force Attack Detection And Prevention On A Network Using Wireshark Analysis. Understanding how computers communicate with one another is a critical point to exploiting network traffic.

Brute Force Dictionary Attack Example Stack Overflow
| Title: Brute Force Dictionary Attack Example Stack Overflow |
| Format: eBook |
| Number of Pages: 302 pages Brute Force Attack Detection Using Wireshark |
| Publication Date: February 2020 |
| File Size: 1.9mb |
| Read Brute Force Dictionary Attack Example Stack Overflow |
 |

How Hackers Could Brute Force Ssh Credentials To Gain Access To Servers
| Title: How Hackers Could Brute Force Ssh Credentials To Gain Access To Servers |
| Format: eBook |
| Number of Pages: 278 pages Brute Force Attack Detection Using Wireshark |
| Publication Date: March 2019 |
| File Size: 1.7mb |
| Read How Hackers Could Brute Force Ssh Credentials To Gain Access To Servers |
 |
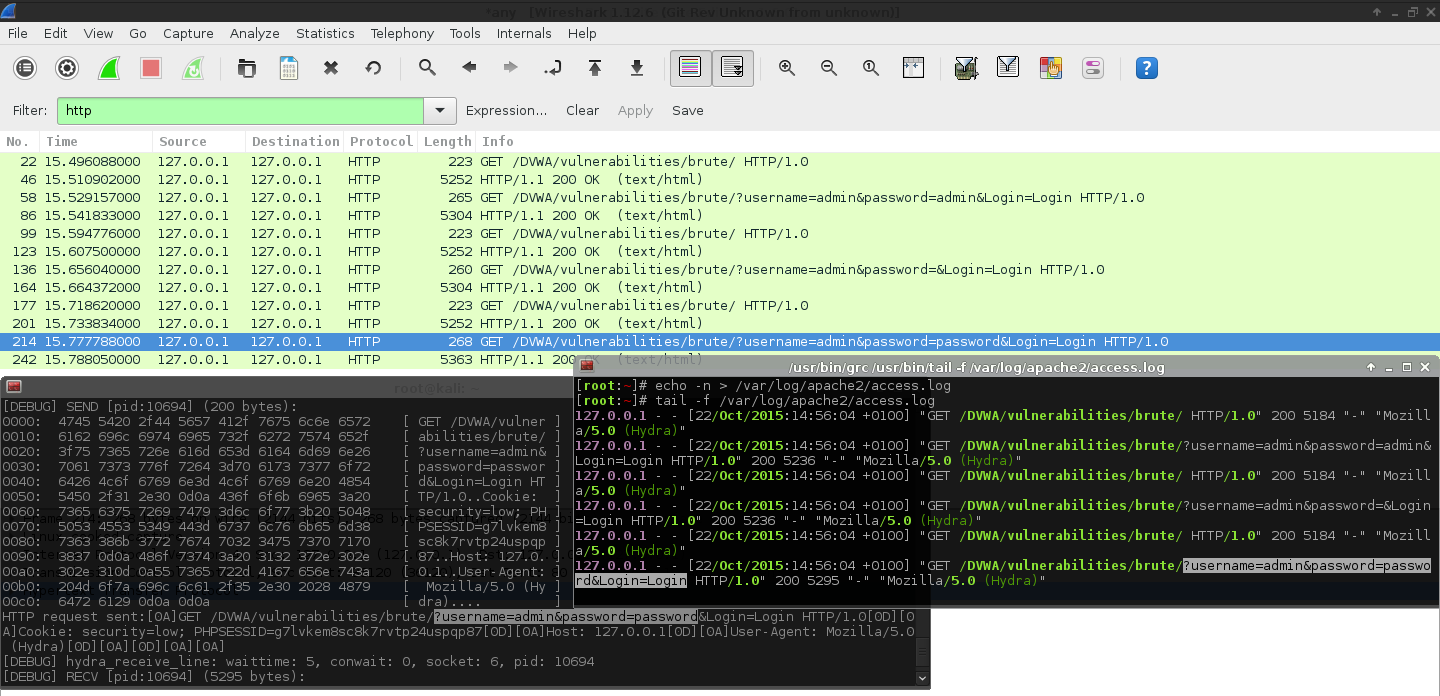
Dvwa Brute Force Low Level Get Form Hydra Patator Burp G0tmi1k
| Title: Dvwa Brute Force Low Level Get Form Hydra Patator Burp G0tmi1k |
| Format: eBook |
| Number of Pages: 287 pages Brute Force Attack Detection Using Wireshark |
| Publication Date: September 2018 |
| File Size: 1.8mb |
| Read Dvwa Brute Force Low Level Get Form Hydra Patator Burp G0tmi1k |
 |
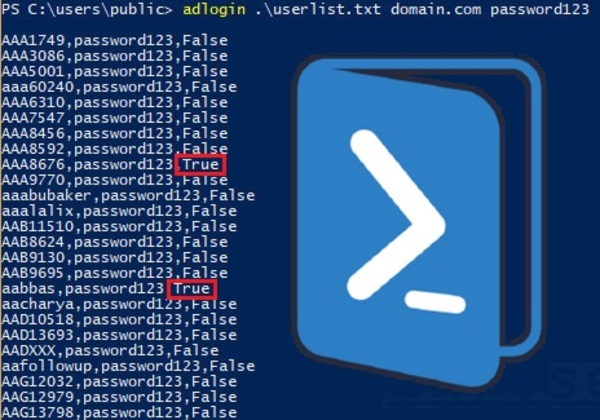
Active Directory Brute Force Attack Tool In Powershell Adlogin Ps1 Infosecmatter
| Title: Active Directory Brute Force Attack Tool In Powershell Adlogin Ps1 Infosecmatter |
| Format: PDF |
| Number of Pages: 191 pages Brute Force Attack Detection Using Wireshark |
| Publication Date: June 2021 |
| File Size: 1.6mb |
| Read Active Directory Brute Force Attack Tool In Powershell Adlogin Ps1 Infosecmatter |
 |
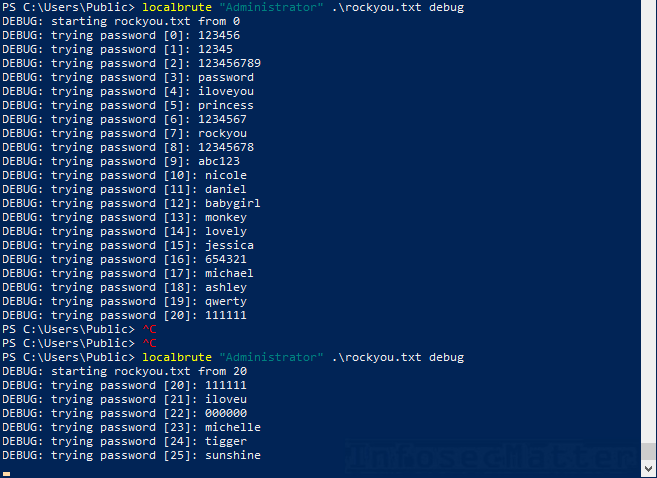
Windows Local Admin Brute Force Attack Tool Localbrute Ps1 Infosecmatter
| Title: Windows Local Admin Brute Force Attack Tool Localbrute Ps1 Infosecmatter |
| Format: eBook |
| Number of Pages: 301 pages Brute Force Attack Detection Using Wireshark |
| Publication Date: August 2020 |
| File Size: 2.2mb |
| Read Windows Local Admin Brute Force Attack Tool Localbrute Ps1 Infosecmatter |
 |
How To Search And Brute Force Services On Non Standard Ports Ethical Hacking And Peration Testing
| Title: How To Search And Brute Force Services On Non Standard Ports Ethical Hacking And Peration Testing |
| Format: ePub Book |
| Number of Pages: 152 pages Brute Force Attack Detection Using Wireshark |
| Publication Date: October 2020 |
| File Size: 1.8mb |
| Read How To Search And Brute Force Services On Non Standard Ports Ethical Hacking And Peration Testing |
 |
Preventing Brute Force Attack Work Projects Work Simulation Tools
| Title: Preventing Brute Force Attack Work Projects Work Simulation Tools |
| Format: eBook |
| Number of Pages: 151 pages Brute Force Attack Detection Using Wireshark |
| Publication Date: March 2017 |
| File Size: 6mb |
| Read Preventing Brute Force Attack Work Projects Work Simulation Tools |
 |

Brute Force Dictionary Attack Example Stack Overflow
| Title: Brute Force Dictionary Attack Example Stack Overflow |
| Format: ePub Book |
| Number of Pages: 162 pages Brute Force Attack Detection Using Wireshark |
| Publication Date: November 2018 |
| File Size: 2.2mb |
| Read Brute Force Dictionary Attack Example Stack Overflow |
 |

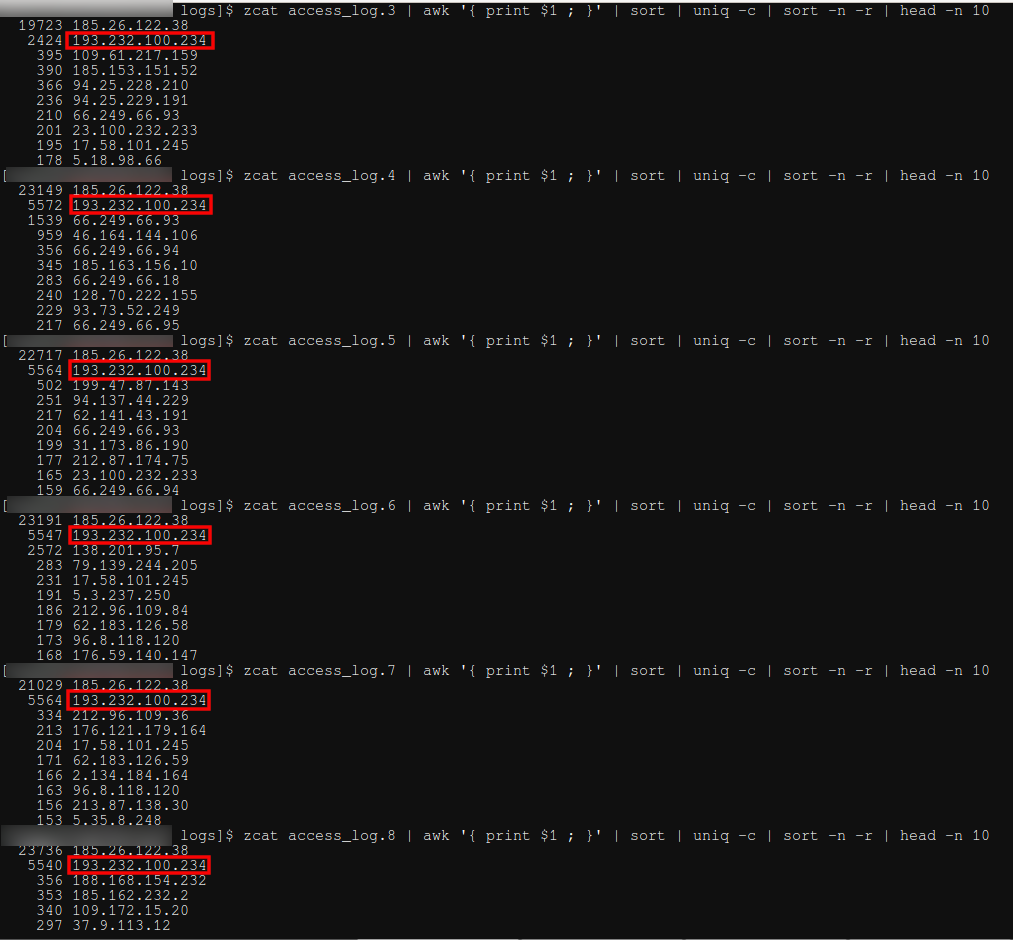
Detect Password Cracking Attempts Wireshark Work Security
| Title: Detect Password Cracking Attempts Wireshark Work Security |
| Format: ePub Book |
| Number of Pages: 261 pages Brute Force Attack Detection Using Wireshark |
| Publication Date: January 2019 |
| File Size: 2.8mb |
| Read Detect Password Cracking Attempts Wireshark Work Security |
 |
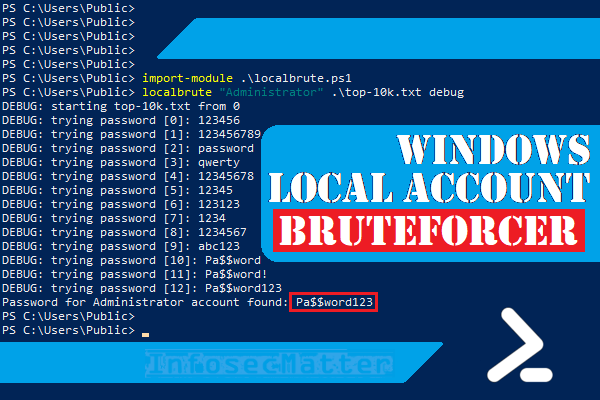
Windows Local Admin Brute Force Attack Tool Localbrute Ps1 Infosecmatter
| Title: Windows Local Admin Brute Force Attack Tool Localbrute Ps1 Infosecmatter |
| Format: PDF |
| Number of Pages: 271 pages Brute Force Attack Detection Using Wireshark |
| Publication Date: December 2018 |
| File Size: 2.8mb |
| Read Windows Local Admin Brute Force Attack Tool Localbrute Ps1 Infosecmatter |
 |

Hydra Post Brute Force For Success Information Security Stack Exchange
| Title: Hydra Post Brute Force For Success Information Security Stack Exchange |
| Format: ePub Book |
| Number of Pages: 259 pages Brute Force Attack Detection Using Wireshark |
| Publication Date: June 2018 |
| File Size: 800kb |
| Read Hydra Post Brute Force For Success Information Security Stack Exchange |
 |
This blog post will use the phrase brute force to reference brute force and dictionary attacks. Brute-force attacks are a prevalent phenomenon that is getting harder to successfully detect on a network level due to increasing volume and encryption of network traffic and growing ubiquity of high-speed networks. The project demonstrates a technique by which brute force attacks on FTP servers can be detected using Wireshark Analysis.
Here is all you have to to learn about brute force attack detection using wireshark Brute force attack using LDAP simple bind. Using this information comparing traffic capture statistics can help to detect successful versus unsuccessful SSH sessions. Brute-force attacks are a prevalent phenomenon that is getting harder to successfully detect on a network level due to increasing volume and encryption of network traffic and growing ubiquity of high-speed networks. Dvwa brute force low level get form hydra patator burp g0tmi1k active directory brute force attack tool in powershell adlogin ps1 infosecmatter how hackers could brute force ssh credentials to gain access to servers windows local admin brute force attack tool localbrute ps1 infosecmatter hydra post brute force for success information security stack exchange how to search and brute force services on non standard ports ethical hacking and peration testing In this detection an alert is triggered when Defender for Identity detects a massive number.